Security
The security and reliability of our service is our number one priority. We only host WordPress and WordPress Multisite, and are fine-tuned to support it.
We handle all WordPress, plugin, and theme security updates. We scan all sites daily for any known vulnerabilities.
Please find our detailed technical and security guide below, and reach out to us with any questions that you may have.
Table of Contents
Datacenters
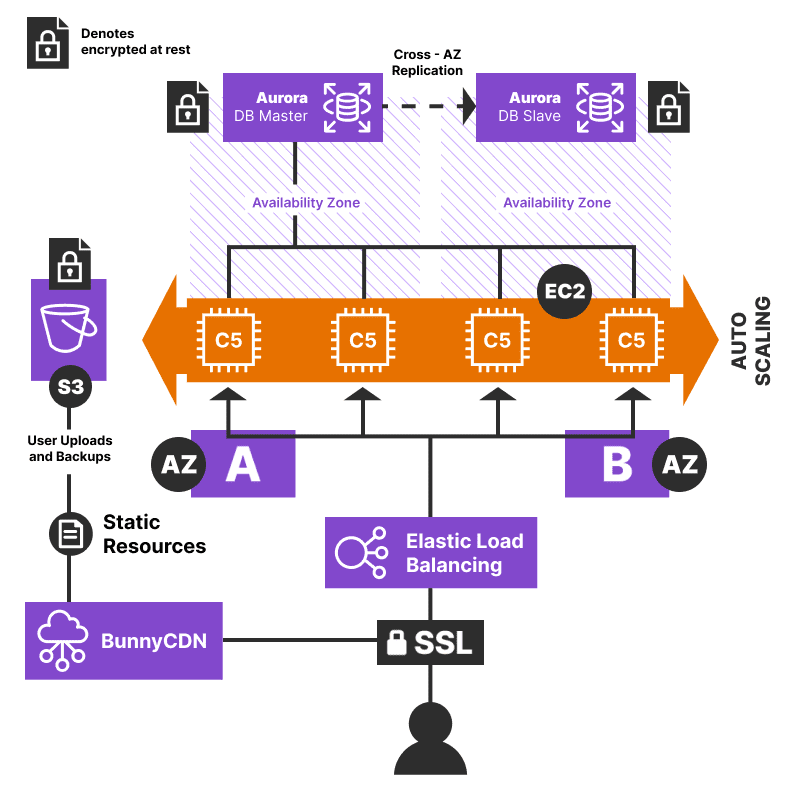
CampusPress manages sites either through our bespoke load balancing auto scalable enterprise grade cluster (deployed through AWS), or fully managed custom compartmentalized and dedicated instances. We can help you decide which environment will best meet your needs, and we handle all the setup and configuration behind the scenes. In general, larger Multisite networks are the best fit for the enterprise cluster and custom individual sites are best on our compartmentalized instance.
With our bespoke enterprise auto scaling option, sites are hosted on a cluster of multiple web and database servers for built-in replication, load balancing, and redundancy. Nightly database backups are encrypted and then stored with Amazon S3.
With our managed and compartmentalized instance, each site gets its own dedicated CPU and memory resources and makes use of incremental backups (for faster restores), staging environments, and optional SFTP and SSH developer access.
In order to comply with local legal and privacy requirements, each customer can choose to be fully hosted in one of the following countries:
- Australia (Enterprise Cluster & Dedicated Instance)
- Canada (Enterprise Cluster & Dedicated Instance)
- Germany (Enterprise Cluster & Dedicated Instance)
- India (Dedicated Instance)
- Japan (Dedicated Instance)
- Netherlands (Dedicated Instance)
- Singapore (Dedicated Instance)
- UK (Enterprise Cluster & Dedicated Instance)
- USA (Enterprise Cluster & Dedicated Instance)
- South Korea (Dedicated Instance)
- France (Dedicated Instance)
All customer data in the WordPress instance(s) will not leave the country in which it is hosted.
CampusPress staff remotely manage and maintain the servers and applications in these datacenters.
CampusPress, and our customers, are able to leverage certifications and security assurances provided by these partners as it relates to physical security. More on compliance and certifications of each can be found at aws.amazon.com/compliance.
All data centers include the highest levels of 24/7/365 on-site security, regulated climate control, redundant power, automated off-site backups, and industry-leading network infrastructure.
Architecture
Bespoke Enterprise Grade AWS Cluster
Sites hosted on this cluster make use of many AWS services including EC2 for web servers, Elastic Load Balancing, Relational Database Service for database servers, and automated scaling when needed.
We use Docker containers with Ansible to isolate each WordPress install from each other, while still allowing each site to benefit from the scalability that comes with our infrastructure. Customers that have the need can be served in fully dedicated private cloud clusters for an additional cost.
Fully Dedicated, Managed, and Compartmentalized Instance
Sites hosted on this instance have their own dedicated virtual server with dedicated IPs, memory, CPUs, and hard disk space. The size of the server depends on the purpose and traffic needs of the site, though we always size up to ensure it can handle peaks in any traffic (in addition to both server and application side caching).
File Scanning and Storage
All images, documents, and other user files are uploaded securely to Amazon S3 to help optimize the performance of server resources. This includes files and uploads from sites hosted on our dedicated and compartmentalized instance.
All user file uploads are scanned using ClamAV for possible virus or malicious files, and any suspicious files are automatically quarantined.
Content Delivery Network (CDN)
All images and files are served via a CDN. Currently, this includes 100+ PoPs of Global BunnyCDN network.
WAF, DDOS Protection, and Firewalls
We utilize a variety of tools and services to monitor and protect the traffic and applications we serve. This includes network firewalls, blocking of malicious IPs, ModSecurity WAF (hosting type dependant), and DDoS mitigation.
Cache and Traffic Spikes
All text content on the public side is cached automatically so that no matter how many visitors your site gets, speeds stay fast. We handle billions of page views each year, and are confident we can handle the largest of any sudden traffic spikes.
Security Practices
Security Breaches
We have no known security breach in our history.
Notification Policy
Should any security-related event occur, our policy is to alert our customers via email no later than 24 hours of our team becoming aware of the event. We will work closely with any customers affected to determine next steps such as end-user notifications, needed patches, and how to avoid any similar event in the future.
SSL & HTTPS (Data In Motion)
Customers can provide their own SSL certificates or we can obtain free certificates via Let’s Encrypt.
Data is encrypted in motion as we require HTTPS for all logged-in traffic and recommend forcing for logged out as well.
Data Storage and Encryption (Data At Rest)
The WordPress database and all backups are encrypted at rest. In addition, sensitive data such as any local user passwords are salted and hashed in the database via standard WordPress practice.
Single Sign-On and Authentication
We encourage the use of single sign-on services to manage all WordPress user accounts and authentication. Supported integrations include Active Directory, LDAP, Shibboleth, CAS, SAML, ADFS, and Google G Suite. We also encourage and support multi-factor authentication capabilities via these integrations.
Other Security Practices
Our dedicated security staff performs daily checks of industry security blogs, websites, and newsletters to keep on top of any potential vulnerabilities that pertain to the systems we use or employ.
We use ClamAV for all servers and TrendMicro and Norton for our desktops with regular updates as needed. We use Patchstack to monitor WordPress vulnerability database.
Disaster Recovery & Backups
Networks on our bespoke enterprise option are hosted on a cluster of multiple web and database servers for built-in replication, load balancing, and redundancy.
Sites on our dedicated and compartmentalized instance are able to be migrated or restored in new virtual server instances within minutes.
All hosted sites and Multisite networks have automated nightly database backups in place which are encrypted and then stored with Amazon S3. Backups are kept for at least 7 days and no more than 30 days. The backup system is manually tested on a bi-weekly basis.
Restore times depend on the size of the WordPress site or network and the cause of the disaster, but full backup recovery should take no more than 24 hours.
Employee Policies
Every CampusPress employee goes through background and reference checks, as well as an on-boarding process that includes a trial period where access to customer servers and data is provided only when working directly under the supervision of another staff member.
CampusPress staff only have access to systems that are directly required to complete the functions of their job. We enforce the use of multi-factor authentication for all critical systems and communications services, and automatically log all staff activity using an internal logging tool and Amazon Cloud Trail.
All CampusPress staff (including any contractors) undergo initial training to ensure proper understanding of all security related processes. Staff regularly attend industry conferences and otherwise stay informed of best practices and relevant trends. Staff agree, in writing, to all policies and procedures annually.
Business Continuity
In short, we are a fully distributed team in 12+ countries and always have backup coverage for all roles in different regions around the world. This allows us to withstand any natural disaster or other events.
WordPress Security
We only host WordPress (an open source web CMS). Customers can contribute their own WordPress plugins/themes which results in a shared responsibility of the codebase and security practices. More details on WordPress security can be found here: https://wordpress.org/about/security.
Any WordPress core security patches will be applied within 24 hours of release.
Custom Plugins and Themes
All plugins and themes developed by our team or included in our curated and approved list (Common Plugins/Themes) undergo a comprehensive code review to check for known vulnerabilities.
For custom plugins and themes requested by clients, our team also performs a detailed code review to check for known vulnerabilities. However, please note the following limitations:
- We do not test custom plugins or themes for compatibility with other themes or plugins used on our server setup.
- Our team is not responsible for maintaining, upgrading, or fixing issues that arise from custom plugins, particularly after upgrades.
- If a vulnerability is identified, we will provide feedback on any necessary fixes required by our team.
For more detailed information, please refer to:
Development
Change Management
In order to ensure the reliability of our service, we’ve implemented a change management policy that we follow for all updates, upgrades, and code changes.
We perform all WordPress core, plugin and theme updates, general improvements, and server maintenance during a regularly scheduled weekly window. All changes are thoroughly tested by our developers and quality assurance team as follows:
- Tested fully in a local testing environment by the technical team.
- Automated and unit testing in multiple development environments.
- Manual testing by the QA team in multiple development environments using all major browsers and operating systems, including mobile devices.
- Full deployment to a small subset of live networks and all development/test networks that willingly participate in our beta testing program.
- Final manual code and performance review by technical team leadership.
- Full deployment to all customers during the next regular ‘Primary Updates’ window (Tuesdays) and an update published to our changelog alerting customers.
- Continuous monitoring by technical and support teams.
For any significant changes that end users may notice, we’ll provide documentation and warning to Super Administrators well in advance.
Code Audits and Guidelines
We have automatic and manual code reviews in place for all plugins and themes that are added to any site we host. All plugins and themes must adhere to the WordPress Coding Standards as well as a list of guidelines that we provide in our documentation section.
Bitbucket & Version Control
We use Bitbucket for version control. Customers that have custom themes should initiate a pull request to alert our team of developers to initiate a code review.
Depending on the queue and complexity of the theme (or edit), a review can take up to 24 hours (or more for complex themes).
Development Environments
We can set you up with a testing environment where you can upload themes or test major changes before moving to production.
For individual sites, our clone tool can be used to create a clone of an existing site that can be used to test a new theme or add new content without affecting your live site.
Service Level Agreements
Reliability and Uptime SLA
We guarantee a 99.9% availability of service. For any month where greater than or equal to 99.9% availability is not obtained, at the customer’s request, a 5% credit of the total annual contract price will be applied to the account. This credit will be applied for the following contract renewal.
Credit will not be applied if the reason for less than 99.9% availability is:
- a result of scheduled outages notified to the Client at a time agreed upon and completed outside of the Client’s normal business hours.
- due to Client authored code, user-generated content, or changes to the Service by parties other than the Host.
- data center interruptions related to acts of God, natural disasters, or outside the control of the Host or the host’s hosting partner(s).
- outages or errors created by 3rd party service providers contracted by the Client (not contracted by the Host), such as Single Sign On providers and similar.
We maintain a list of Level 1 outages that affect a significant number of customers at status.campuspress.com.
Support SLA
All support is handled via email at contact@campuspress.com. Some customers on higher plans may also choose to setup shared slack channels for more real-time communication to aid in support.
End-user email support (ie. faculty, staff, student) is not normally provided directly and must be explicitly included in the package or license purchased. The customer is encouraged to forward support requests from end-users should additional help be needed to resolve the issue.
Our support staff will triage all incoming support requests 24/7 according to the following levels:
Level 1 – Critical
Complete inability to access or use the platform, both the frontend and the backend of the entire network.
Level 2 – High
The frontend is available, but the backend is such that updates to sites can’t be made on the entire network. Or, one or more sites are completely unavailable, but not the entire network.
Level 3 – Medium
Partial or limited loss of non-essential functionality affecting all users. An example would be media files not being able to be uploaded by users.
Level 4 – Low
An inconvenience that does not impact general performance. An example would be one plugin or theme not working correctly, but otherwise, the site is up and running without errors.
While we will work to reply to all support requests, at all levels, as quickly and completely as possible, the following SLA guarantees are in place:
Level 1 – 1st reply within 30 minutes with updates every 30 minutes until resolution.
Level 2 – 1st reply within 1 hour with updates every 1 hour until resolution.
Level 3 – 1st reply within 4 hours with updates each day until resolution.
Level 4 – 1st reply within 24 hours with updates every 48 hours until resolution.
For any calendar month where these guarantees are not met 2 (two) or more times, at the customer’s request, CampusPress agrees to apply a 5% credit to the account to be applied towards the following renewal.